1.2.5.7. Test the New Firewall Rules¶
Once again you will generate traffic through the BIG-IP AFM and then view the AFM (firewall) logs.
- Ping 10.30.0.50
- Open a new Web browser and access http://10.30.0.50
- Open a new Web browser and access http://10.30.0.50:8081
- SSH to 10.30.0.50 using Web Server shortcut (PUTTY) on desktop.
In the Configuration Utility, open the Security > Event Logs > Network > Firewall page.
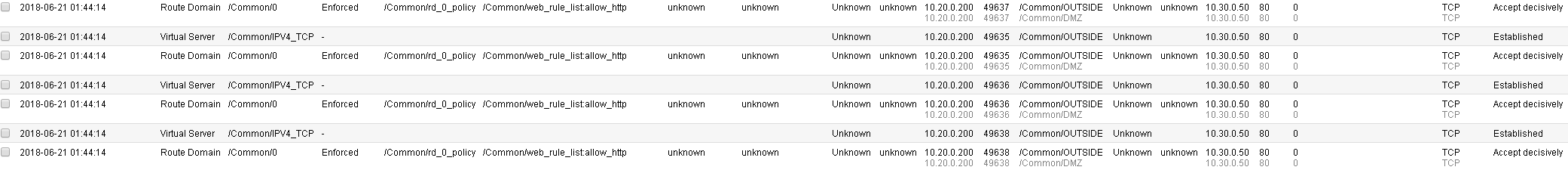
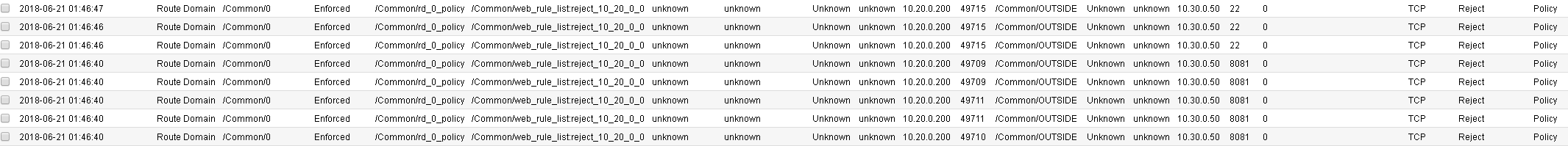
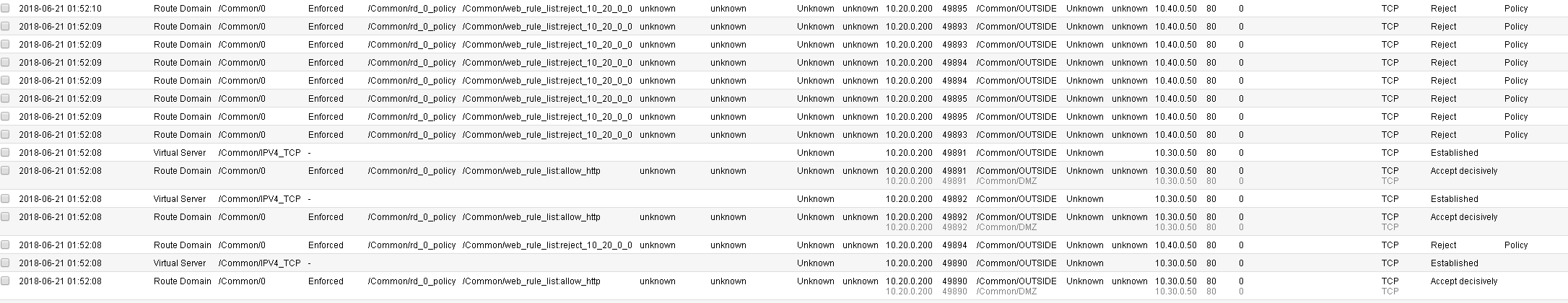
Access for port 80 was granted to a host using the web_rule_list: allow_http rule.
Requests for port 8081, and 22 were all rejected due to the reject_10_20_0_0 rule.
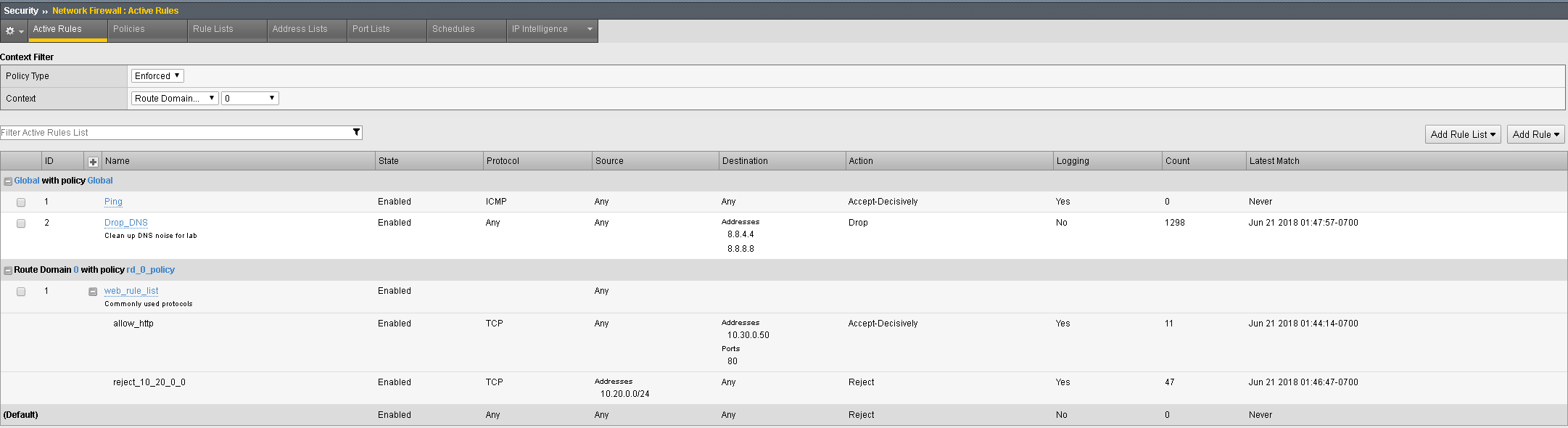
You may verify this, by going to Security > Network Firewall > Active Rules, then selecting the context for route domain 0. Note the Count field next to each rule as seen below. Also note how each rule will also provide a Latest Matched field so you will know the last time each rule was matched:
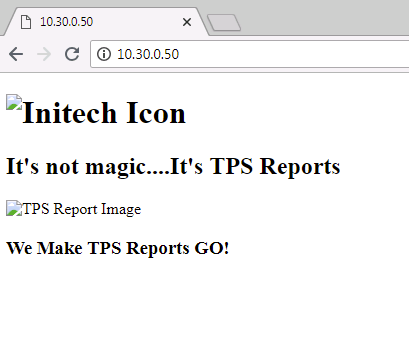
Congratulations! Day one and you’ve already saved the day. Hang on, something isn’t right, the images Mr. Lumbergh talked about are not populating, they look like broken links.
Let’s refresh the web page once more and see what the logs show….
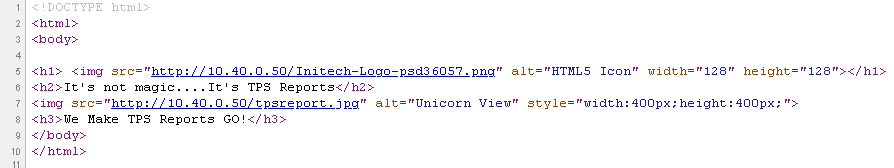
If we follow the flow we can see the traffic to 10.30.0.50 is permitted on port 80 however; there appears to be a second connection attempting to open to another server, 10.40.0.50, also on port 80 (glad we put in that reject rule and are logging all the traffic flows). Let’s look at how this web page is written. To view the page source details, simply right click anywhere on the 10.30.0.50 web page and select “view page source”
Very interesting, it appears there are two images and they are links to another server which appear to be a server on the application network, which is also a link off of the firewall. You can verify this by looking at the network settings on the BIG-IP found under: Network > VLANs and/or Network > Self IPs. To resolve, let’s create another rule list for this network as well to keep the rule lists separated for security reasons.